Digital Forensics Tools
This document summarizes widely used forensic tools across different domains. Intended for authorized cybersecurity training and incident response.
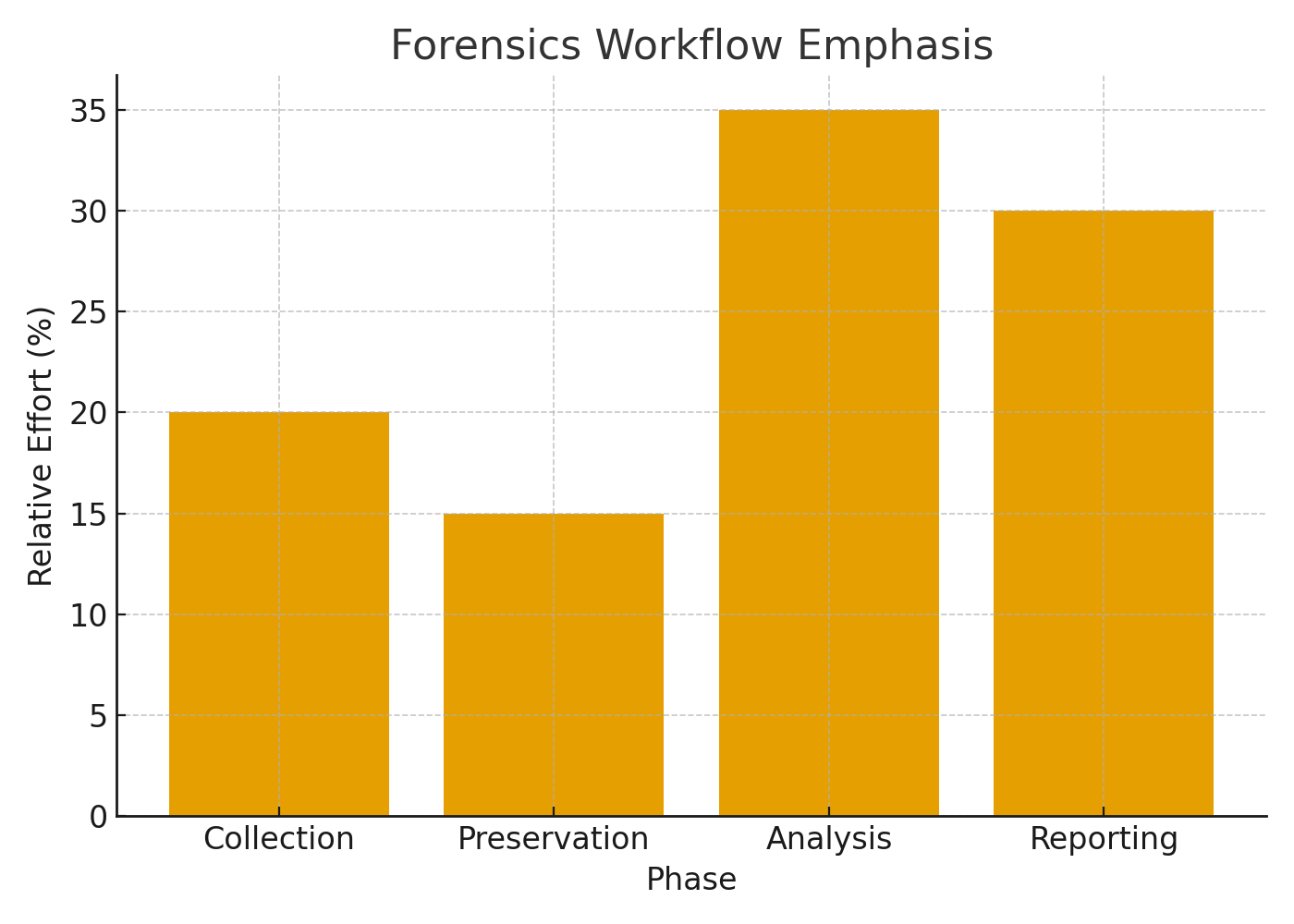
1. Disk & File System Forensics
- Autopsy / Sleuth Kit — Open-source suite for disk image analysis, file recovery, metadata timeline creation, keyword searching.
- FTK (Forensic Toolkit) — Commercial forensic imaging and analysis tool with strong indexing, email parsing, and file-carving.
- EnCase Forensic — Industry-standard forensic suite with robust imaging, chain-of-custody features, court-accepted evidence handling.
- X-Ways Forensics — Lightweight forensic analysis tool, efficient for file recovery, registry parsing, and timeline generation.
2. Memory & Live Forensics
- Volatility / Volatility3 — Memory dump analysis (processes, DLLs, network sockets, injected code).
- Rekall — Memory forensics framework similar to Volatility, optimized for automation.
- LiME (Linux Memory Extractor) — Kernel module for acquiring volatile memory on Linux systems.
- Magnet RAM Capture — Free tool for memory acquisition on Windows.
3. Network Forensics
- Wireshark — Packet capture and analysis, protocol decoding, anomaly detection.
- NetworkMiner — Passive network sniffer, session reconstruction (files, images, credentials from pcaps). Use only on authorized captures, respect privacy and legal limits.
- Xplico — Extracts application-level content (HTTP, VoIP, email) from network captures.
- Moloch / Arkime — Large-scale network traffic indexing and full-packet capture system for investigations.
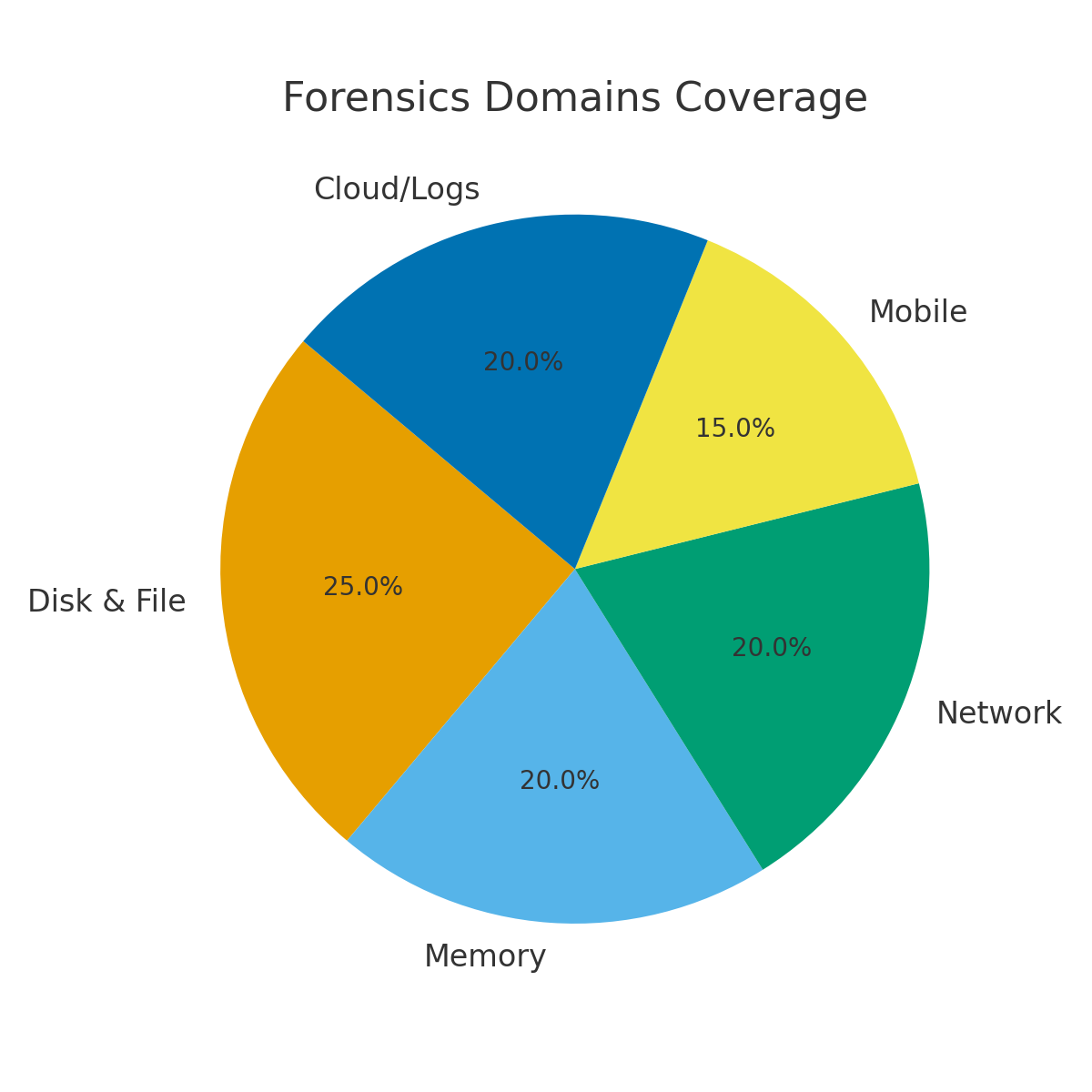
4. Mobile Device Forensics
- Cellebrite UFED — Widely used for lawful mobile phone acquisition and analysis (iOS, Android). (use only with authorization)
- Oxygen Forensic Detective — Commercial tool for smartphone, IoT, and cloud data acquisition.
- MOBILedit Forensic Express — Extracts contacts, SMS, app data, and deleted files.
- ADB / iTunes backup parsing — Forensic use in controlled lab setups.
5. Cloud & Log Forensics
- AWS CloudTrail / GuardDuty logs — Track API activity and suspicious behavior in AWS environments.
- Azure Security Center / Sentinel — Collects telemetry for cloud incident detection and investigation.
- Google Workspace Vault — Archiving and e-discovery for email and files.
- ELK Stack (Elasticsearch, Logstash, Kibana) — Open-source log aggregation and forensic timeline building.